LOOK WHO’S TROLLING NOW —
Authorities who took down the ransomware group brag about their epic hack.
Dan Goodin
– Feb 20, 2024 9:29 pm UTC

Getty Images
After years of being outmaneuvered by snarky ransomware criminals who tease and brag about each new victim they claim, international authorities finally got their chance to turn the tables, and they aren’t squandering it.
The top-notch trolling came after authorities from the US, UK, and Europol took down most of the infrastructure belonging to LockBit, a ransomware syndicate that has extorted more than $120 million from thousands of victims around the world. On Tuesday, most of the sites LockBit uses to shame its victims for being hacked, pressure them into paying, and brag of their hacking prowess began displaying content announcing the takedown. The seized infrastructure also hosted decryptors victims could use to recover their data.
Enlarge / The dark web site LockBit once used to name and shame victims, displaying entries such as “press releases,” “LB Backend Leaks,” and “LockbitSupp You’ve been banned from Lockbit 3.0.”
this_is_really_bad
Authorities didn’t use the seized name-and-shame site solely for informational purposes. One section that appeared prominently gloated over the extraordinary extent of the system access investigators gained. Several images indicated they had control of /etc/shadow, a Linux file that stores cryptographically hashed passwords. This file, among the most security-sensitive ones in Linux, can be accessed only by a user with root, the highest level of system privileges.
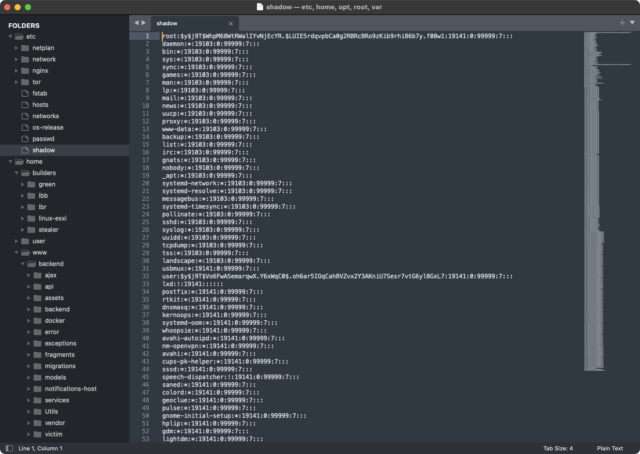
Enlarge / Screenshot showing a folder named “shadow” with hashes for accounts including “root,” “daemon,” “bin,” and “sys.”
Other images demonstrated that investigators also had complete control of the main web panel and the system LockBit operators used to communicate with affiliates and victims.
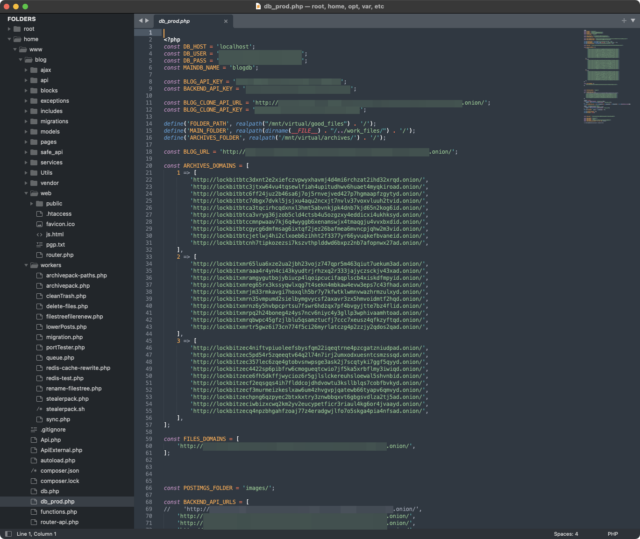
Enlarge / Screenshot of a panel used to administer the LockBit site.
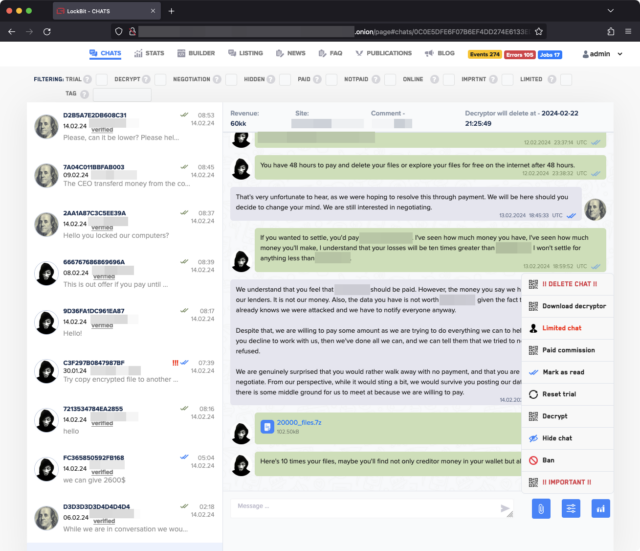
Enlarge / Screenshot showing chats between a LockBit affiliate and a victim.
The razzing didn’t stop there. File names of the images had titles including: “this_is_really_bad.png,” “oh dear.png,” and “doesnt_look_good.png.” The seized page also teased the upcoming doxing of LockbitSupp, the moniker of the main LockBit figure. It read: “Who is LockbitSupp? The $10m question” and displayed images of cash wrapped in chains with padlocks. Copying a common practice of LockBit and competing ransomware groups, the seized site displayed a clock counting down the seconds until the identifying information will be posted.

Enlarge / Screenshot showing “who is lockbitsupp?”
In all, authorities said they seized control of 14,000 accounts and 34 servers located in the Netherlands, Germany, Finland, France, Switzerland, Australia, the US, and the UK. Two LockBit suspects have been arrested in Poland and Ukraine, and five indictments and three arrest warrants have been issued. Authorities also froze 200 cryptocurrency accounts linked to the ransomware operation.
“At present, a vast amount of data gathered throughout the investigation is now in the possession of law enforcement,” Europol officials said. “This data will be used to support ongoing international operational activities focused on targeting the leaders of this group, as well as developers, affiliates, infrastructure, and criminal assets linked to these criminal activities.”
LockBit has operated since at least 2019 under the name “ABCD.” Within three years, it was the most widely circulating ransomware. Like most of its peers, LockBit operates under what’s known as ransomware-as-a-service, in which it provides software and infrastructure to affiliates who use it to compromise victims. LockBit and the affiliates then divide any resulting revenue. Hundreds of affiliates participated.
According to KrebsOnSecurity, one of the LockBit leaders said on a Russian-language crime forum that a vulnerability in the PHP scripting language provided the means for authorities to hack the servers. That detail led to another round of razzing, this time from fellow forum participants.
“Does it mean that the FBI provided a pen-testing service to the affiliate program?” one participant wrote, according to reporter Brian Krebs. “Or did they decide to take part in the bug bounty program? :):).”
Several members also posted memes taunting the group about the security failure.
“In January 2024, LockBitSupp told XSS forum members he was disappointed the FBI hadn’t offered a reward for his doxing and/or arrest, and that in response he was placing a bounty on his own head—offering $10 million to anyone who could discover his real name,” Krebs wrote. “‘My god, who needs me?’ LockBitSupp wrote on January 22, 2024. ‘There is not even a reward out for me on the FBI website.’”
>>> Read full article>>>
Copyright for syndicated content belongs to the linked Source : Ars Technica – https://arstechnica.com/?p=2004713










