Moving to the cloud had clear advantages—but only if done right. Done wrong, your investment could leave your organization open for attack. These tips will help mitigate those risks.
Supporting enterprise security during a cloud migration can be rife with pitfalls that can derail the initiative and ruin the customer experience.
It’s no joke—I know a finance director who suffered this fate. She joined the company in the middle of a corporate cloud transformation initiative and inherited a new Privileged Access Management (PAM) solution as part of an enterprise cybersecurity overhaul. Over the next year, she struggled to implement even the most basic PAM cybersecurity use cases. As the transformation journey progressed, the PAM solution failed to deliver. The solution couldn’t accommodate new hybrid IT demands and use cases.
As you can imagine, she had to end the initiative. Cutting the cord was painful for her. It’s so important to understand the shift in business processes. You need to ask the important questions:
How will employees and vendors access systems and applications?
Where will those resources live?
What attack surfaces are exposed?
How are cyberattack methods evolving?
You must also understand how moving to cloud drives changes in enterprise cybersecurity—how to protect those resources, drive down risk, and improve productivity.
Read on to learn more about these challenges and explore 10 extended PAM capabilities essential to supporting enterprise security during a cloud migration.
What is cybersecurity for the enterprise?
Cybersecurity for the enterprise is the technology, processes, and tactics necessary to protect your business resources from misuse and abuse by cyber attackers. This includes both physical and logical (software) security.
Cybersecurity for the enterprise is a critical aspect of doing business in our online and connected world. Enterprise cybersecurity is a vast landscape (image below). We’ve all invested in these areas, yet we’re still being breached. So, with a limited budget, where should we focus? What’s the best return on our cybersecurity investment that takes the biggest bite out of cyberattack risk?
Delinea
This blog will focus on logical security controls for enterprise resilience in the form of Privileged Access Management (PAM).
Imagine a world where all your personal and business information is at the mercy of hackers, where a single click on a malicious link can cause irreparable damage. Of course, you don’t have to imagine. This is the reality we live in today.
Systems and data are on premise and in the cloud. An explosion of workstations, servers, containers, IoT, and mobile devices has opened opportunities for hackers to exploit. Tapping the cloud means adopting a “shared responsibility model” where IT has less direct control and visibility over the IT stack. Technology has advanced to a point where even the smallest business has become vulnerable to cyberattacks.
The good news is just as cyberattacks have evolved, so has the technology to protect your business and customers. Investing in robust enterprise cybersecurity can empower your team to focus on your business goals rather than constantly putting out fires associated with cyberattacks.
Investing in the right tools to protect your systems and sensitive data
Enterprise cybersecurity can be expensive and time-consuming, but let me ask you this: What’s the cost of a ransomware attack on your business? Aside from the ransom, a single data breach can cost millions in business impact and recovery, damage to your reputation, and possible fines and litigation. IBM’s Cost of a Data Breach reports that costs can also accrue an average of 24% of data breach costs in the subsequent two years.
So, invest in the right tools to protect your systems and sensitive data.
Business transformation has made cybersecurity more challenging. Putting your faith—and your budget—in the wrong place can result in substandard protection, increased operational overhead and costs, and compliance gaps. As your business modernizes, transforming to take advantage of cloud services, so must your enterprise cybersecurity posture.
PAM cybersecurity—exceptional value for your limited budget
A reasonable approach is to understand where cyber attackers invest most of their efforts and focus on that as the most significant attack surface. Verizon’s annual Data Breach Investigation Report is one of many respected publications with a solid finger on the pulse of incidents and breaches. Verizon has consistently reported that compromised credentials are involved in 70-80% of data breaches and ransomware attacks worldwide.
Throwing more money at network-centric security is not the answer. It’s more logical and better business sense to invest in identity-centric security to protect access to privileged accounts, workstations, and servers.
Not all PAM cybersecurity solutions are up to the challenge, however. To support your modern enterprise, we need a similarly modern PAM with extended capabilities to address these new use cases.
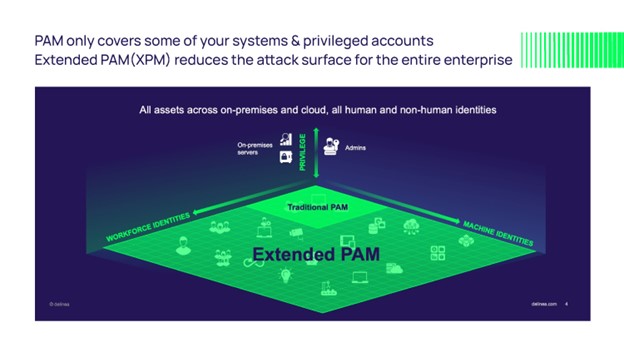
Delinea
As we heard earlier from the finance organization executive, you don’t want to fall foul of a solution that struggles to embrace the hybrid cloud nature of your business. You must be clinical and critical in your evaluation.
Lifting and shifting an enterprise application into the cloud does not guarantee the SaaS and PaaS benefits of performance, scalability, and elasticity necessary for a modern business. This also holds for PAM vendors shoehorning a decade-old PAM product into virtual machines in the cloud.
Checklist: 10 capabilities of extended PAM in enterprise cybersecurity
There are several characteristics of an extended PAM solution designed to tackle this and make your business more resilient to cyberattacks. Not all are new; several have been in PAM for years. However, a modern PAM redesign is critical to ensure parity.
Comprehensive PASM and PEDM
The two critical components of PAM are secure remote access with credential vaulting and host-enforced privilege elevation. Analysts like Gartner refer to these as Privileged Account and Session Management (PASM) and Privilege Elevation and Delegation Management (PEDM). It would be best if you had both, especially in support of best practices such as zero trust and zero standing privileges. Ensure your vendor has not short-changed PEDM, putting most of their R&D budget into PASM.
2. Cloud-native PAM cybersecurity platform
We’ve already mentioned limited IT budget and value for money. Derive significant value with a cloud-native PAM platform. Compared to standalone enterprise PAM cybersecurity products, you benefit from substantial economies, including:
Better performance
Increased reliability
Reduced application overhead
Shared services consistency
Centralized management
Faster innovation
Cost reduction
Easier compliance
Futureproofing
3. Options: Cloud-native SaaS or on-premise vault
Some organizations prefer to run the vault in their data center for complete control over its operation, performance, and scalability. Others prefer a SaaS vault running on a PAM platform to ensure easy reach for all users, internal or third party, and reduce operational overhead and infrastructure costs.
To ensure high performance and scalability, a native cloud service can leverage underlying PaaS (Platform-as-a-Service) services, such as auto-scaling and failover availability zones. Remember that scale and performance requirements will differ for human users versus apps and services. In a DevOps context, programmatic access to vault services will be more demanding.
4. Client-based password rotation and reconciliation
If you search through the PAM annals of history, you’ll see that on day-1, password rotation was a foundational vault requirement. Today, all vaults implement this by requiring a local or domain-level administrator account to log in and rotate passwords on each server. These back-door attack vectors contravene best practices like zero standing privileges and zero trust, increasing your attack surface.
A modern PAM approach combines PASM and PEDM. The vault instructs the PEDM client to rotate locally. This is more elegant and avoids opening new doors for adversaries to exploit. It also introduces another benefit; the vault can ask the local PAM client to validate a vaulted password before checkout or session initiation. If they’re out of sync, the client can reconcile to ensure the user isn’t denied access.
5. Just-in-time access workflows
When removing implicit trust to support zero trust and the principle of least privilege, we must provide administrators a way to obtain elevated confidence when necessary. Enterprise-level PAM cybersecurity solutions satisfy this requirement with self-service request workflows for explicit approval. However, it’s essential to couple “just-in-time access” with temporary “just-enough privilege.” I.e., constrain privileges to only what’s necessary for the task and automatically de-provision them to prevent standing privileges.
The default workflows to fulfill this requirement will be built into the PAM solution. However, a modern PAM can also defer to an external workflow, such as ServiceNow, to incorporate PAM workflows into broader IT workflows.
6. Passwordless authentication
A modern PAM cybersecurity solution must support several existing passwordless methods such as PKI, SSH keys and certs, and FIDO2 dongles. Building authentication services and MFA into the PAM platform (see above) enables rapid innovation and support for newer standards such as Passkeys.
7. Multi-factor authentication
Multi-factor authentication (MFA) is recognized as a critical weapon in the PAM cybersecurity arsenal. It helps confound cyber criminals in two main ways; multiple factors are harder to hack, and the authenticator is harder to obtain or replicate. Providing extra identity assurance, MFA helps determine friend from foe and block bots and malware from escalating privileges and moving laterally.
While PAM cybersecurity products have supported MFA for a while, it tends to be limited to MFA on vault login. However, several laws, regulations, and industry recommendations demand or strongly recommend MFA for high-risk access and protecting server data. For example, PCI-DSS, the U.S. Government in its Federal zero trust strategy, and GDPR.
Also, you may find yourself ineligible for new cyber risk insurance or a policy renewal if you’re not using MFA for remote and privileged access.
Look for MFA as a PAM platform service that can be enforced at all significant access gates:
PASM:
Vault login
Secret access
Remote session initiation
PEDM:
Server log in
Privileged command and application execution
8. Secure access for remote employees and third-party vendors
Exploiting VPN accounts to breach networks has been popular for decades. One of the most notable cases was the Target company breach in 2013. What better tactic than to compromise a more vulnerable partner? When the COVID-19 pandemic hit, organizations had to react fast when offices closed; buying more VPN licenses was a knee-jerk response. When VPN access exploded, adversaries were gifted a larger attack surface and a lower security hurdle.
A modern PAM solution should support secure remote access without a VPN or SSH and RDP clients and servers—just a browser, no client apps. This improves security (backed by MFA) plus less friction for remote employees and vendors.
9. One identity to rule them all—identity consolidation
Rarely do enterprise administrators have just one account. Especially in Linux estates, they create multiple local privileged accounts for convenience. Each is a potential attack vector, increasing your attack surface. We can eliminate them and enforce least privilege, allowing admins to log in to any system (Windows, Linux, or UNIX) with a single enterprise account.
An extended PAM with multi-directory brokering supports accounts from multiple identity providers. You can embrace a traditional directory like Active Directory, OpenLDAP, or a cloud directory such as Azure AD, Ping Identity, or Okta. Isolate third-party identities from employee accounts and more easily incorporate new identity providers, a merger or acquisition, or cloud migration.
10. Disaster recovery
If you lose access to vaulted credentials and secrets, systems and applications become unavailable, and the business suffers. In the unlikely case of infrastructure failure, automatic replication to another on-premise or cloud-hosted vault instance ensures continuous availability. Seamless failover and faster disaster recovery always ensure break-glass access to secrets. This must be built into the PAM solution.
Here’s an extra consideration for the road: analytics-informed policies
User productivity is severely underserved in legacy PAM solutions. There are several ways an extended PAM can address this, such as automating manual processes, self-service workflows, and intelligent access control policies.
PAM cybersecurity solutions that support traditional static rules and policies require constant care and feeding to ensure they’re current and comprehensive. This puts a heavy burden on IT and can impact users by not being adaptive to their context. This can also be a pain for users if rules are binary, i.e., MFA is always on or off. Always on may be overkill, introducing unnecessary steps when logging in or running privileged apps and commands.
By learning “typical” user behavior, behavioral analytics with machine learning can identify anomalous behavior in real-time and create a risk score. Thus, access policies can be as simple as:
Low risk: let the user in with no challenge
Medium risk: ask for proof via a second factor
High risk: deny access and alert the security team
In summary, the right PAM solution as part of a broader enterprise cybersecurity program will enable your business. It will drive resilience to combat threats without slowing down your cloud transformation. Audits for compliance will be more streamlined. PAM will be more invisible, automating processes to reduce operational overhead, costs, and friction for DevOps and end users.
Learn more about Delinea Extended Privileged Access Management.

Tony Goulding
>>> Read full article>>>
Copyright for syndicated content belongs to the linked Source : CIO – https://www.cio.com/article/1251425/cybersecurity-for-enterprise-10-essential-pam-considerations-for-modern-hybrid-enterprises.html










