Small- and medium-sized businesses and enterprises have accelerated their move into the cloud since the global pandemic. The Infrastructure-as-a-Service (IaaS) cloud computing model enables remote working, supports digital transformation, provides scale, increases resilience, and can reduce costs. However, this shift requires a thorough understanding of the security implications and how a business can protect its data and applications.
As with all technology introductions, it’s important to have clear security policies, tools, processes, and training. Cloud infrastructure is especially sensitive, as many critical applications are at risk, such as customer-facing applications. Companies that have embraced the cloud need to understand the Shared Responsibility Model: a security and compliance framework that explains what shared infrastructure and systems the cloud provider is responsible for maintaining and how a customer is responsible for operating systems, data, and applications utilizing the cloud. Unless the model is understood and followed, it could lead to data, applications, and cloud workloads being exposed to security vulnerabilities.
Good Dog Communications in Partnership with Verizon and Edgio recently hosted a webinar, “The Rise of Cloud Exploitation, ” that spoke directly to cyberthreats targeting web apps and security best practices. Watch on-demand here.
How is the cloud being attacked and why?
Cloud exploitation involves targeting vulnerabilities in cloud infrastructure, applications, or services to gain unauthorized access, disrupt operations, steal data, or carry out other malicious activities. A cloud exploitation playbook could include attack vectors like distributed denial-of-service (DDoS) attacks, web application attacks, and bots – with the number one attack target being web applications. According to the 2023 Verizon Data Breach Investigations Report (DBIR), the majority of cyber attacks are led by organized criminals looking to disrupt business and steal data to sell. The number one reason (95%) for cyber attacks is financial gain, with 24% of all cyber attacks involving ransomware.
Common cloud exploitation outcomes
Unauthorized Access: Attackers may attempt to gain unauthorized access to cloud accounts, systems, or data by exploiting weak or stolen credentials, misconfigurations, or vulnerabilities in the cloud environment. Once inside, they can potentially access sensitive information, modify data, or launch further attacks.
Data Breaches: Cloud exploitation can result in data breaches, where attackers gain access to sensitive data stored in the cloud. This can occur due to insecure configurations, inadequate access controls, or vulnerabilities in cloud storage or databases. The stolen data can be used for various malicious purposes, such as identity theft, financial fraud, or corporate espionage.
Distributed Denial of Service (DDoS): Attackers may launch DDoS attacks against cloud services or applications, overwhelming them with a high volume of malicious traffic or requests. This can lead to service disruptions, making the cloud resources unavailable for legitimate users.
Malware Distribution: Cloud exploitation can involve hosting or distributing malware through cloud-based platforms or services. Attackers may upload malicious files or applications to cloud storage or use cloud infrastructure to propagate malware to unsuspecting users.
Account Hijacking: Cloud exploitation can involve the compromise of user accounts, allowing attackers to gain control over cloud resources. This can occur through techniques like phishing, social engineering, or exploiting vulnerabilities in authentication mechanisms. Once an account is hijacked, attackers can abuse the cloud resources for their own purposes or launch attacks from within the compromised account.
What can businesses do? Respond to threats with speed
Threat detection and mitigation speed are important for three key reasons. First, adversaries are adept at learning from open-source intelligence to develop new tactics, techniques, and procedures (TTPs) making rapid security response imperative. Second, cyber criminals are well-organized and act fast. Verizon’s 2023 DBIR noted, “more than 32% of all Log4j scanning activity over the course of the year happened within 30 days of its release (with the biggest spike of activity occurring within 17 days).” And, finally, the importance of speed is clearly illustrated by the fact that companies that contain a security breach in less than 30 days can save $1M or more.
To reduce the risk of cloud exploitation, it is crucial that businesses implement strong security measures, such as robust access controls, encryption, regular security assessments, and monitoring of cloud environments. Implementing Web Application and API Protection (WAAP) at the edge is critical to identifying and mitigating a variety of threats such as DDoS attacks, API abuse, and malicious bots. Modern-day WAAPs utilize machine learning and behavioral and signature fingerprinting for early threat detection. Further, companies using AI and automation see breaches that are 74 days shorter and save $3 million more than those without.
A WAAP rapid threat detection and mitigation solution is an invaluable tool for DevSecOps teams to implement an optimized “Observe-Orient-Decide-Act” (OODA) loop to improve:
Meantime to Detect (MTTD) and
Meantime to Respond (MTTR) as new threats arise.
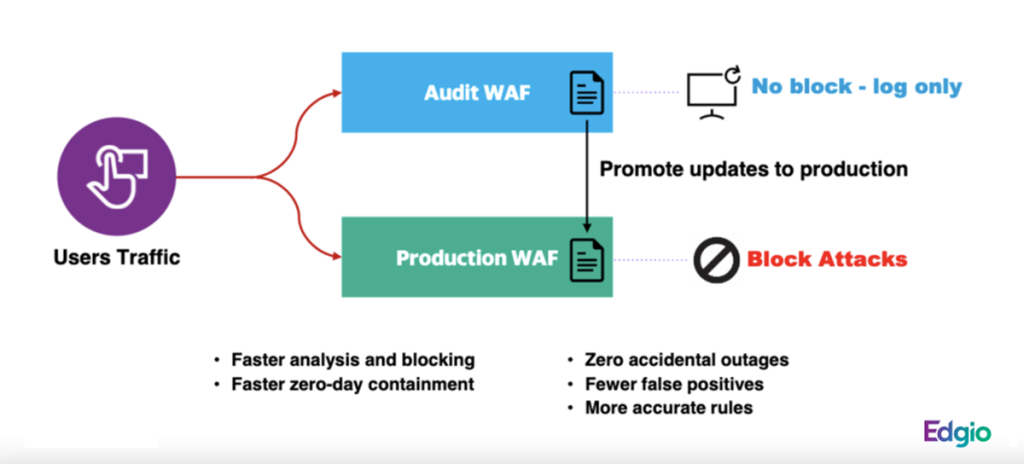
The latest innovation is a “Dual WAAP” capability that enables DevSecOp teams to test new rules in audit mode against production traffic to verify their effectiveness while lowering the risk of blocking legitimate site traffic. This increased confidence, plus the ability to integrate with existing CI/CD workflows, allows teams to push effective virtual patches out faster, closing the door on attackers more quickly than ever before. Additionally, with Dual WAAP, there is no WAAP downtime while updating rulesets, with new rules deployed across the global network sometimes in under 60 seconds.
Edgio
The hidden threat: open-source code
The Verizon DBIR noted that exploited web application vulnerabilities account for 5% of breaches. These web application vulnerabilities can stem from codebases that use open-source code. In the Verizon webinar, “The Rise of Cloud Exploitation”, Edgio’s Richard Yew, Senior Director, Product Management – Security, highlighted findings from the 2023 Synopsys report that showed the extent of open source code and how much risk exists in legacy applications. Here are some shocking findings:

Edgio
To close
Cloud Infrastructure-as-a-Service has brought extreme agility to organizations. However, cloud exploitation is on the rise and it is clear from the Shared Responsibility Model that companies are partners in ensuring a secure enterprise. Cloud service providers play a crucial role in securing the cloud infrastructure, but companies must apply solutions to enhance security and protect against exploitation of operating systems, applications, endpoints, and data.
A powerful choice in the cyberthreat fight is a WAAP solution. It offers rapid threat detection and mitigation and is an invaluable tool for DevSecOps teams to implement an optimized “Observe-Orient-Decide-Act” (OODA) loop to improve both mean time to detect (MTTD) and mean time to respond (MTTR) as new threats arise.
Edgio is a global edge platform with 300+ Points of Presence and 250+ Tbps of capacity that helps companies build, secure, and deliver amazing app experiences. Its WAAP security platform enables organizations to implement effective security into modern web applications, innovate faster and mitigate risks with its unified, multi-layer approach. Talk to an expert to protect your cloud applications today.
>>> Read full article>>>
Copyright for syndicated content belongs to the linked Source : CIO – https://www.cio.com/article/646452/how-to-manage-cloud-exploitation-at-the-edge.html










