Senior managers at an ‘Achilles heel’ local authority for Europe’s biggest nuclear site ‘still don’t know what was lost’ in a 2017 cyber attack, according to a council source

By
Tommy Greene
Published: 19 Oct 2023 14:15
Copeland Borough Council, which has in recent months been reorganised into Cumberland Council, was hit by a wave of WannaCry ransomware attacks in May 2017 that caused havoc at a number of UK public service providers over a bank holiday weekend.
The following year, Copeland bosses told the BBC that no sensitive data had been taken as part of the cyber attack, which was then thought to have cost the local authority around £2m.
However, a council source said senior managers have told staff in the years following those press statements, during IT induction sessions, that they “still don’t know who did it and what [information] was lost” during the 2017 attack.
The US and the UK have attributed the WannaCry ransomware campaign, which hit hospitals and local authorities in Britain, to North Korea. The North Korean advanced persistent threat group known as Lazarus, thought to be behind WannaCry, has
since been linked
to a number of other high-profile cyber attacks targeting medical research bodies and energy firms.
Copeland Borough Council and the new Cumberland authority are in many ways unremarkable rural local authorities. But they are unique in holding extensive documents that include sensitive information about Sellafield, Europe’s biggest nuclear site.
The council source, who wished to remain anonymous, described Copeland and Cumberland as a potential “Achilles heel” for the facility, which stores 70-75% of the UK’s most radioactive waste.
Alongside extensive planning information, Copeland also held considerable operational data on Sellafield, which directly employs more than 11,000 people, the vast majority of whom are based at Seascale, along the Cumbrian coast.
Operational data held by the two Cumbrian councils can cover the movement of nuclear inventory, waste management, planning information and services provided to Sellafield by contractors.
The most recent audit report for the council, produced by consultancy firm Grant Thornton, highlighted a number of failings and a disjointed culture in Copeland’s finance department, which a councillor said also extended to its IT function.
Joseph Gayouba, a former councillor at Copeland and elected representative at the new Cumberland authority, told Computer Weekly there was a lack of continuity across the former organisation, extending to Copeland’s IT function.
“According to Grant Thornton’s audit reports on Copeland, there was a heavy reliance on agency staff to carry out critical roles,” he said. “This added costs to the organisation and caused problems with business continuity and organisational stability.”
Computer Weekly understands that, following the 2017 ransomware attack, Copeland brought in a permanent IT manager in a bid to address concerns around cyber security vulnerabilities.
Copeland bosses pointed to the 2017 cyber attack as a key factor behind the council’s failure to submit audited accounts for four consecutive years. It was cited again last week, by the council’s legacy auditor, as a “discrepancy” of £8m was highlighted in its books.
Years of financial disarray at Copeland have contributed to a £28.9m shortfall in the new Cumberland authority, which was established in April this year.
Cyber security failings
A significant oversight in Copeland’s IT regime, the Grant Thornton report found, was its lack of a disaster recovery plan before and after the 2017 cyber attack.
Computer Weekly asked Cumberland to confirm whether it holds a disaster recovery plan for the new combined authority, which covers much of west Cumbria – including Sellafield sites. At the time of publication, Cumberland said it held an “emergency plan”, but had not provided further details of the document, nor a copy of it.
Russell Price, chair at the Continuity Forum, pointed out that it was “remiss” of the council not to hold such a critical protocol document.
“A local authority is a ‘Category 1 Responder’ under the Civil Contingencies Act,” he said. “If there was an incident, there are obligations on them around disaster recovery, business continuity, incident management [and so on] that are most definitely Category 1 Responders’ responsibilities.”
Price added that funding cuts from central government, recruitment challenges and a slowness to adapt to cyber security threats across the UK’s public sector during these years helped explain why Copeland was left exposed to such threats.
He said, however, that the council handled communications poorly when it publicly claimed that no sensitive data had been lost at the time, before this had been confirmed.
“That is the antithesis of good practice according to the various national and international standards that exist,” said Price. “If you don’t know or are unsure, you should say you don’t know, that you’ll find out, and communicate it as soon as you find out. That is a legitimate answer, even if it’s painful and puts people under pressure.”
WannaCry attack
Islington and Salisbury Councils, along with 80 of England’s 236 NHS trusts at the time, were among those hit by the WannaCry ransomware over the 2017 May bank holiday weekend, as hackers demanded a bitcoin ransom to gain access to encrypted files.
According to Copeland Borough Council, some processes at the local authority were not restored until almost a year later.
The attack has been blamed for the financial problems that have beset the council in recent years, which have seen it approach Whitehall for a number of “capitalisation directives” and forcing it to dip into capital reserves to pay day-to-day running costs.
The embattled council did not file audited accounts for any of the final four years it was operating, before being subsumed into the new Cumberland authority.
Karl Connor, who worked as a Copeland councillor and communications manager at Sellafield during this time period, told Computer Weekly council officers had given assurances to elected representatives that no critical information had been lost.
“I would go as far as to say that the council was woefully under-resourced when it came to knowledge around cyber security and disaster recovery. It was a small council and it just didn’t have the expertise to manage something like this”
Karl Connor, ex-councillor at Copeland and ex-communications manager at Sellafield
He believes they did not fully grasp the extent of what had happened at the time. “Council members were given reassurances by officers that this was going to be okay. Honestly, I don’t think those officers would have deliberately lied, but I believe that they didn’t understand the full extent of what was happening, and how bad it was, at the time this was going on,” he said.
“I would go as far as to say that the council was woefully under-resourced when it came to knowledge around cyber security and disaster recovery. It was a small council and it just didn’t have the expertise to manage something like this,” said Connor.
He also told Computer Weekly that, despite much of the council’s business and internal conversations concerning Sellafield and wider security issues, there was no consideration – that he was aware of – given to potential cyber security vulnerabilities in relation to Sellafield prior to the attack.
“I can’t say categorically that it was definitely never discussed, but I’m not aware of these issues ever having been discussed by either organisation prior to the event itself,” said Connor.
“As a small council, Copeland had a seat at some national tables that a council of its size wouldn’t ordinarily merit. So I think there was a desire – rather than direct pressure from Sellafield – to be seen as having things under control once the attack had happened.”
A spokesperson for Sellafield and the Nuclear Decommissioning Authority (NDA) told Computer Weekly that neither body, to its knowledge, has shared any information classified as ‘Sensitive Nuclear Information’ level with Copeland Borough Council.
The spokesperson said: “As part of the UK civil nuclear sector, we are subject to a strong nuclear safety and security regulatory scheme, which requires us to meet robust legal and national security requirements.
“We have no reason to believe any data related to the NDA or Sellafield was compromised in the 2017 Copeland Borough Council cyber incident.”
Meanwhile, an Office for Nuclear Regulation spokesperson said: “We would not envisage any local authority having the need to hold sensitive nuclear information about a nuclear site.”
Price said the new unified Cumberland authority “should prioritise a more coordinated strategy” around cyber security protections, wider resilience measures and business continuity.
He added: “It seems that Copeland Borough Council did not have a mature, well-proven, business continuity plan, as recommended in the Civil Contingencies Act, that would broadly conform to the standard that is specifically cited in the guidance.
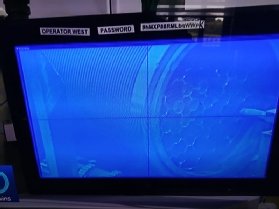
A password for a Sellafield computer system displayed on a piece of equipment at the facility was broadcast live to millions of poeple
“That’s what they should have been aiming for, and it remains a top-priority question for the unitary authority. They need to be able to show how [these] things have changed habits, and be able to show real change – not just having folks turning up and saying, ‘Oh, no. We’re on top of this.’
“They need to be able to demonstrate evidence and show that there is not any lingering false confidence at play.”
Cumberland Council conceded, in response to Computer Weekly’s queries, that it does not yet have a disaster recovery plan in place.
A spokesperson for the council said: “We cannot comment on the actions of Copeland Borough Council or their response to the cyber attack.
“At Cumberland Council, we take the security of our IT systems very seriously and have multiple levels of security across all of our IT systems.
“These are constantly tested, reviewed and updated. In the event of an incident affecting our IT systems, these would be dealt with in accordance with the plans in place from the former councils. A corporate disaster recovery plan for Cumberland Council is being developed.”
Read more on Data breach incident management and recovery

Lancaster Uni lends cyber support to nuclear decommissioning body

By: Alex Scroxton

Hyperoptic, Community Fibre take gigabit highway to Islington

By: Joe O’Halloran

Sellafield Ltd inks network services contract with BT

By: Joe O’Halloran

Hackney Council could be forced to answer questions about IT security training after Psya ransomware

By: Bill Goodwin
>>> Read full article>>>
Copyright for syndicated content belongs to the linked Source : Computer Weekly – https://www.computerweekly.com/news/366555634/Sellafield-local-authority-unsure-if-data-was-stolen-six-years-on-from-North-Korea-ransomware-attack










